LAN switches and BUM traffic
Before understanding the VLAN concept, you must first have an understanding of two core concepts about the Ethernet standard - what is a broadcast domain and what is BUM traffic. Let's start with the BUM data type. BUM stands for broadcast, unknown unicast, and multicast. When a LAN switch receives a frame that belongs to one of these types, it sends the frame to all its ports except the port it received the frame on. This behavior is shown on figure 1.
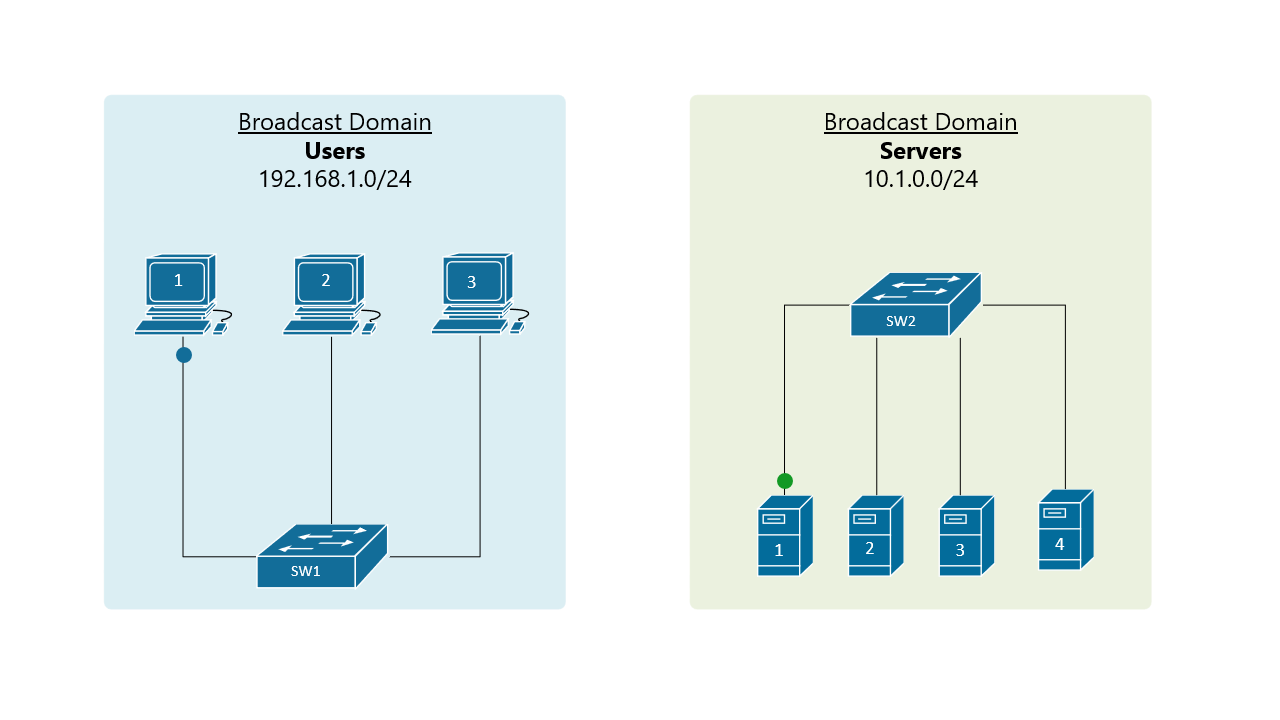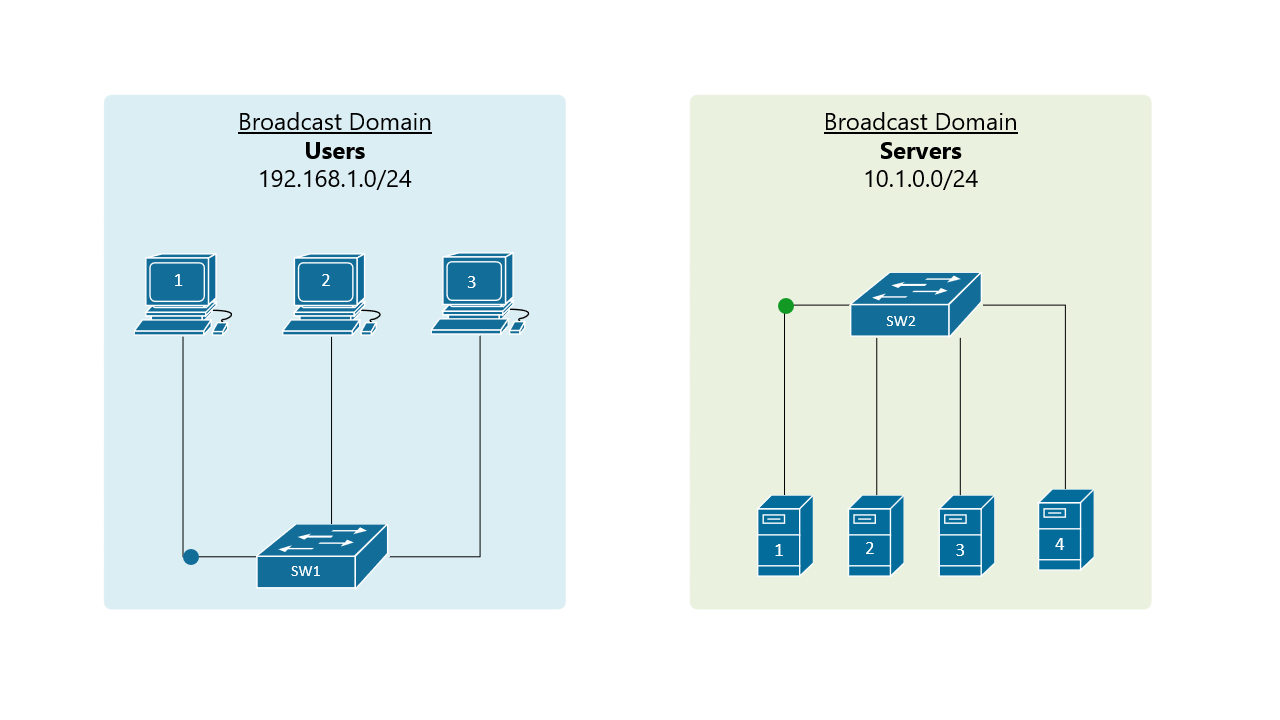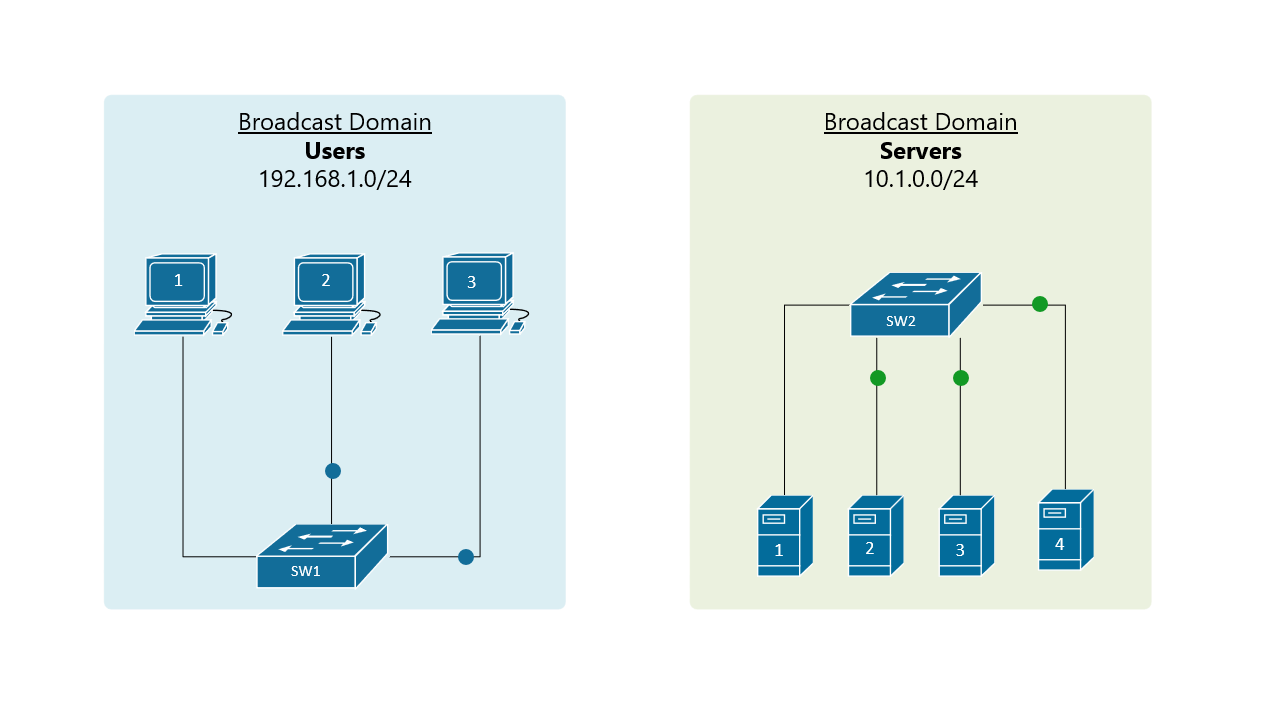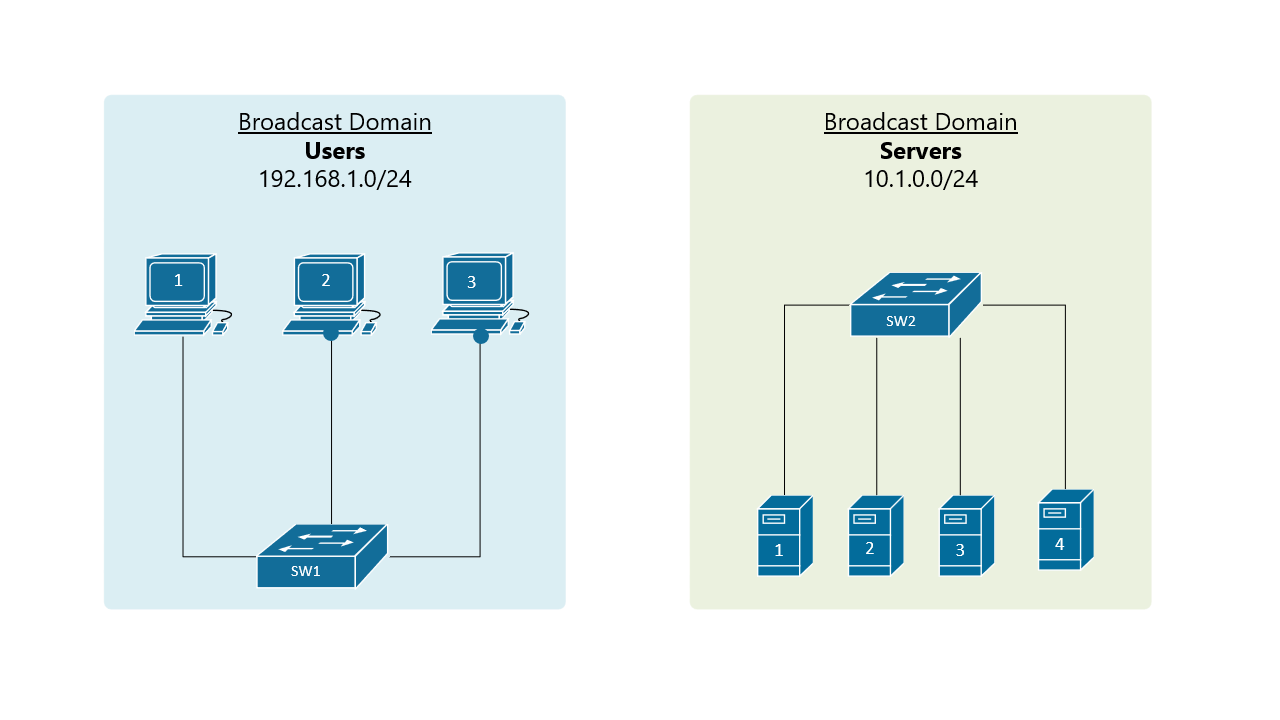
A broadcast domain includes all connected devices that get a copy of any broadcast, unknown unicast, or multicast (BUM) frame being sent. In the above figure, the blue LAN on the left is one broadcast domain and the green LAN on the right side is another broadcast domain. A general rule of thumb is that a single LAN is equal to a Broadcast Domain is equal to a Subnet.
LAN = Broadcast Domain = Subnet
By default, all interfaces on a Cisco switch are in the same broadcast domain. Therefore, when a broadcast frame is received on any switch port, the switch forwards it out to all its other ports. Having that logic in mind, to create two separate LANs (like one for servers and one for users), you must use two different switches as shown in figure 1. Тhis approach is not scalable, imagine if your organization want to have thousand separate LANs, it has to have thousands of physical switches. This scaling limitation is the reason why Virtual LANs were introduced.

By using VLANs, a single switch can act as two logical switches or creating two broadcast domains. This is done on a port-by-port basis. Using figure 2 as an example, the ports where the users are connected, are configured to be part of VLAN10 (or in other words to be connected to virtual switch 10) and the ports where the servers are connected to, are configured to be part of VLAN20 (or in other words to be connected to virtual switch 20). The switch will then never forward a frame send by any user to any of the servers and vice-versa because they are part of different broadcast domains.

Benefits of using VLANs
Using VLANs not only improves the scaling of the campus LAN. It has many more advantages such as:
- It improves the security by reducing the number of end-stations that receive copies of BUM traffic.
- It creates smaller fault domains by isolating different groups of devices in separate broadcast domains.
- It reduces the CPU overhead on each device in the LAN by limiting the number of broadcast frames received.
- It improves network performance and speed of failure recovering.
Creating VLANs on a Cisco switch
Cisco switches do not require any initial configuration to work. You just unbox the device, install the cabling, power it up and it works. By default, all interfaces are in VLAN1. This means that all devices connected to the switch are in the same broadcast domain and must be in one subnet. This logic also applies if you connect multiple default setting switches together. They create one multiswitch broadcast domain and all connected clients must be in the same IP subnet. At some point, you will need to connect clients that are in different subnet though. This means that VLANs must be created.
To configure VLANs on a Cisco switch, additional configuration must be added. There are two main steps for creating new VLAN:
- Step 1. Create a new VLAN in the switch VLAN database
- In global configuration mode, we use the vlan [vlan-id] command to create the new VLAN in the switch's database.
- (Optional) In VLAN configuration mode, we use the name [name] command to assign a name to the VLAN.
- Step 2. Assign interfaces to the newly created VLAN.
- In global configuration mode, we use the interface [number] command to move into the interface configuration mode.
- We then use the switchport access vlan [id] to specify the VLAN number associated with the interface.
- (Optional) We use switchport mode access to make the port always operate as an access port.
For this example we will use the following topology. We will create two VLANs - VLAN10 named CLIENTS and VLAN20 named SERVERS and will assign four access ports to each VLAN as shown in Figure 4.

First let's look at the default VLAN database.
Switch#show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/1, Fa0/2, Fa0/3, Fa0/4
Fa0/5, Fa0/6, Fa0/7, Fa0/8
Fa0/9, Fa0/10, Fa0/11, Fa0/12
Fa0/13, Fa0/14, Fa0/15, Fa0/16
Fa0/17, Fa0/18, Fa0/19, Fa0/20
Fa0/21, Fa0/22, Fa0/23, Fa0/24
Gig0/1, Gig0/2
1002 fddi-default act/unsup
1003 token-ring-default act/unsup
1004 fddinet-default act/unsup
1005 trnet-default act/unsup
Note two important things - by default, there are 5 undeletable VLANs. VLAN1 cannot be deleted but can be used. By default all interfaces of the switch are assigned to it. VLANs 1002-1005 cannot be deleted and cannot be used. You can see that their status is “unsp” which stands for unsupported. This means that these VLANs are completely unusable these days. They are leftovers from the days of FDDI and Token Rings.
Let's create VLAN10 and VLAN20 using step1 from the previous section.
Switch#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#vlan 10
Switch(config-vlan)#name CLIENTS
Switch(config-vlan)#exit
Switch(config)#vlan 20
Switch(config-vlan)#name SERVERS
Switch(config-vlan)#end
Switch#show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/1, Fa0/2, Fa0/3, Fa0/4
Fa0/5, Fa0/6, Fa0/7, Fa0/8
Fa0/9, Fa0/10, Fa0/11, Fa0/12
Fa0/13, Fa0/14, Fa0/15, Fa0/16
Fa0/17, Fa0/18, Fa0/19, Fa0/20
Fa0/21, Fa0/22, Fa0/23, Fa0/24
Gig0/1, Gig0/2
10 CLIENTS active
20 SERVERS active
1002 fddi-default act/unsup
1003 token-ring-default act/unsup
1004 fddinet-default act/unsup
1005 trnet-default act/unsup
If you compare the output of show clan brief with the previous one, you can see VLAN10 and VLAN20 are created, but there are no ports assigned to them. All ports are still assigned to the default VLAN 1. Let's assign interfaces to the newly created VLANs as per the example diagram.
Switch#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#interface range fastEthernet 0/1 - 4
Switch(config-if-range)#switchport access vlan 10
Switch(config-if-range)#switchport mode access
Switch(config-if-range)#exit
Switch(config)#interface range fastEthernet 0/15 - 18
Switch(config-if-range)#switchport access vlan 20
Switch(config-if-range)#switchport mode access
Switch(config-if-range)#end
Switch#show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/5, Fa0/6, Fa0/7, Fa0/8
Fa0/9, Fa0/10, Fa0/11, Fa0/12
Fa0/13, Fa0/14, Fa0/19, Fa0/20
Fa0/21, Fa0/22, Fa0/23, Fa0/24
Gig0/1, Gig0/2
10 CLIENTS active Fa0/1, Fa0/2, Fa0/3, Fa0/4
20 SERVERS active Fa0/15, Fa0/16, Fa0/17, Fa0/18
1002 fddi-default act/unsup
1003 token-ring-default act/unsup
1004 fddinet-default act/unsup
1005 trnet-default act/unsup
Now we can see that interfaces Fa0/1 through Fa0/4 are assigned to VLAN10 and interfaces Fa0/15 through Fa0/18 to VLAN20. Let's see whether clients in VLAN10 can ping each other.
C:\>ipconfig
FastEthernet0 Connection:(default port)
Link-local IPv6 Address.........: FE80::20A:41FF:FE83:371A
IP Address......................: 192.168.1.10
Subnet Mask.....................: 255.255.255.0
Default Gateway.................: 0.0.0.0
C:\>ping 192.168.1.11
Pinging 192.168.1.11 with 32 bytes of data:
Reply from 192.168.1.11: bytes=32 time<1ms TTL=128
Reply from 192.168.1.11: bytes=32 time<1ms TTL=128
Reply from 192.168.1.11: bytes=32 time<1ms TTL=128
Reply from 192.168.1.11: bytes=32 time<1ms TTL=128
Ping statistics for 192.168.1.11:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Obviously they are reachable but let's try to ping one of the servers.
C:\>ping 10.1.0.10
Pinging 10.1.0.10 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.
Ping statistics for 10.1.0.10:
Packets: Sent = 4, Received = 0, Lost = 4 (100% loss)
We can see that client 1 cannot ping server 1, because they are part of different VLANs now. The switch acts as two logical switches with the clients connected to logical switch VLAN10 and the servers connected to logical switch VLAN20 as shown in figure 2.

To forward data between the VLANs, we need to use either layer 3 switch or a router, which we are going to do in the next lesson.
Summary
- LAN switches forward any BUM frame to all its ports except the port it received the frame on. This process is called flooding.
- By default all connected devices are in the same broadcast domain (Vlan1). This is a scaling limitation and security vulnerability.
- VLANs were introduced in order to separate device into different broadcast domains.
- A general rule of thumb is that a VLAN = Broadcast Domain = Subnet.
- VLANs are configured and assigned per interface.
It the next lesson we are going to talk about how VLANs work across multiple switches.
Full Content Access is for Registered Users Only (it's FREE)...
- Learn any CCNA, DevNet or Network Automation topic with animated explanation.
- We focus on simplicity. Networking tutorials and examples written in simple, understandable language for beginners.